😂Dynamic Testing of iOS application
To begin Dynamic testing first we have to hook the application using Objection.
For hooking techniques just follow these steps:
Connect your jailbroken iOS device to your laptop.
Use the command
frida-ps -Uaito get a list of all apps currently installed on the connected USB device.

Look for the DVIA application in the list and note its name.
Use the command
objection -g "DVIA-v2" exploreexplore to connect to the application.Use the
envcommand to view the environment variables for the application, including its path.

Check for Sensitive Information saved by the application in the filesystem.
Verify the presence of sensitive information in various locations, including plist files, the Firebase database, keychains, device logs, app screenshots, and cookies.
Sensitive Data in Plist file- Locate sensitive data in the plist file using the framework Objection by typing
env, then navigating to the ‘data directory’, then to the ‘Documents’ folder, and finally using the commandios plist userInfo.plistas shown below.


Sensitive Data in UserDefaults- Similarly type
lsinLibrarythencdintoPreferencesthen againlsand then use commandios plist can com.highaltitidehacks.DVIAswiftv2.plistas shown below.


Sensitive Data in Keychain- Once the user is logged in, developer can store his username and password to the keychain to access the application using keychain. We can dump the keychain using
ios keychain dump_rawcommand which gives us the hexadecimal value then we have to decode this using hex to ascii convertor.




Sensitive Data in Database- Developer can save sensitive data such as username and password in client side database. Locate the Sqlite database at client side and use the command
sqlite connect DatabaseName.sqlitesthen use.tablesto enumerate column names thenselect * from 'ColumName'to see the data in columns.



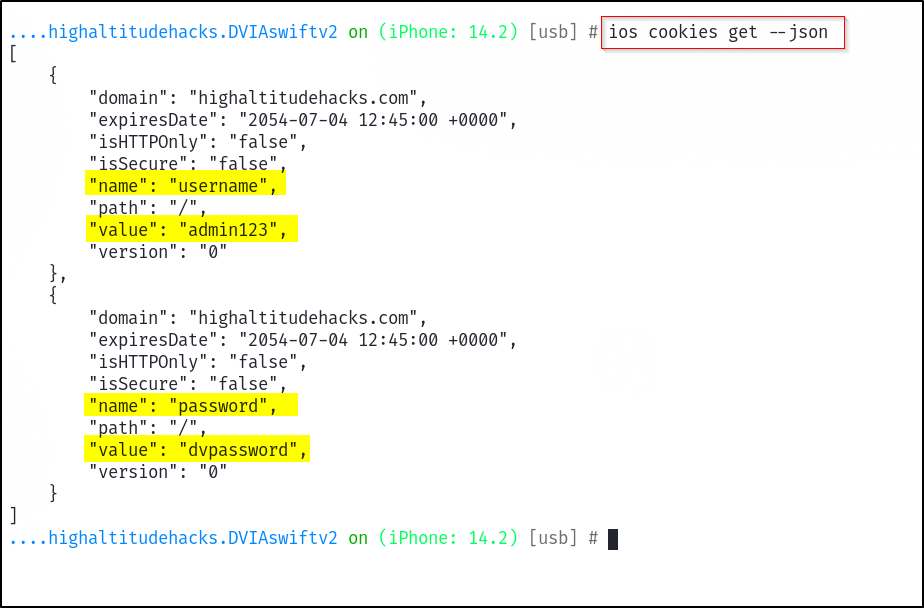
Sensitive Data in Cookies- Sometimes the data can get saved in cookies. We can access it using the command
ios cookies get --json .


Sensitive Data in Device Logs- Make sure to always check logs of any application to do this we use
idevice_idcommand to find the id of the iOS device then use the commandidevicesyslog -u idevice_id | grep "application name"we can also store the logs we just have to use > operator the command will beidevicesyslog -u idevice_id | grep "application name" > logs.txt.


Unfortunately the DVIA-v2 application was crashing always when i was clicking on the Sign Up button hence we are not able to see the data in the logs.
Sensitive Data in App Screenshots- Whenever you press the home button, iOS takes a snapshot of the current screen to be able to do the transition to the application on a much smoother way. However, if sensitive data is present in the current screen, it will be saved in the image (which persists across reboots). These are the snapshots that you can also access double tapping the home screen to switch between apps. Locate the screenshot folder in the application and download the file using command
file download filename.



2. Broken Cryptography
Saving sensitive data in local storage and encrypting it with a hardcoded or predictable key in the code is not a secure practice. This can be easily reversed by attackers, allowing them access to the confidential information. Additionally, developers should avoid using deprecated algorithms for authorization checks, data storage, or data transmission. These include algorithms such as RC4, MD4, MD5, and SHA1, which are no longer considered secure and may leave data vulnerable to attack. It’s important to use current, secure algorithms and best practices to protect sensitive data.
The main check is to moniter the crypt libraries using objection so that we can find which algorithm was used to encrypt the data. We can use Objection command
ios monitor crypt.


3. Local Authentication using Keychain
The iOS keychain APIs can be used to implement local authentication. During this process, the app stores either a secret authentication token or another piece of secret data identifying the user in the keychain. In order to authenticate to a remote service, the user must unlock the keychain using their passphrase or fingerprint to obtain the secret data.
Sometimes we can easily bypass the local authentication check using objection command
ios ui biometrics_bypass.



4. Jailbreak Detection Bypass- We are going to bypass the jailbreak detection using 3 methods.
Using Tweaks- For this we are going to use the HideJB tweak. Open the Settings app on your iOS device > Locate the HideJB preferences > Tap on “Select Apps” > Toggle on the button next to the app name that you want to hide the jailbreak status for, as shown in the screenshot.Make sure you close the running app after starting the HideJB to bypass the detection.






Using Objection- Run the
ios jailbreak disablecommand in the Objection console > Try to access the application you wish to bypass the jailbreak detection for > If successful, the jailbreak detection will be bypassed and you will be able to access the app


Understanding the application jailbreak detection logic -
To understand the application’s logic of jailbreak detection:
Use the command
ios hooking search jailto find the jailbreak detection classes.Use the command
ios hooking list class_methods ClassNameto list the methods within the classes here our classname is “JailbreakDetection”Use the command
ios hooking watch method "+[ClassName MethodName]" --dump-args --dump-backtrace --dump-returnto observe the method. Only--dump-returnwill suffice to determine the value it returns. Here our classname is “JailbreakDetection” and method name is “isJailbroken” If the method returns 0x1, it means it is returning a boolean value of 1, indicating that the device is jailbroken.Now we have to create custom script to bypass this logic , use the command
ios hooking generate simple ClassNameto write a custom script that will change the return value of this method.Copy the generated script from the previous step. Open a text editor and paste the script. Modify the variable value from ‘var’ to ‘const’ then within the ‘onLeave’ function, enter ‘retval.replace(0)’ to return the value of 0. Save the script with the ‘JBbypass.js’ extension and our script should look like this in the 4th screenshot.
Use the Frida command
frida -l JBbypass.js -n "DVIA-v2" -Uto execute the script and bypass the jailbreak detection.






In the same way, we can bypass jailbreak detection in another class named “DVIA_v2.JailbreakDetectionViewController”, which contains 5 methods that return different values. However, this class is implemented in Swift, so we cannot hook it directly using Objection or Frida. The logic of jailbreak detection in iOS is similar to root detection in Android. In iOS, jailbreak detection checks for the presence of specific binary files on the device. If these files are present, it indicates that the device is jailbroken. We can find online script for this and can bypass using frida.




5. SSL Pinning Bypass- We are going to bypass SSL Pinning using 2 methods. Make sure proxy is enabled and running as shown in the envirnoment setup step.
Using Tweaks- For this we are going to use the SSL Kill Swtich 2 tweak. Open the Settings app on your device. > Locate the SSL Kill Switch 2 preferences. > Toggle on the button next to ‘Disable Certificate Validation’ > Use the Burp Suite to capture the request. Make sure you close the running app after starting the SSL Kill Swtich 2 to bypass the SSL Pinning.



Using Objection- Simply use the objection command
ios sslpinning disableand you will be able to capture the application traffic.



Tools List:
Linux — libmobiledevice, Frida, Objection, MOBSF, SSH,Burp Suite,Checkra1n.
iOS — Cydia Manager, Hide JB, Frida, Appsync Unified, Otool,SSL Kill Switch 2, OpenSSH
Last updated