😆Vulnerability #13: Intercepting Implicit intent to load arbitrary URL
For this vulnerability, let’s focus on the ProductList activity and its related parts. Checking the source for the mentioned activity reveals that it registers a broadcast receiver which listens for the com.insecureshop.action.PRODUCT_DETAIL intent:

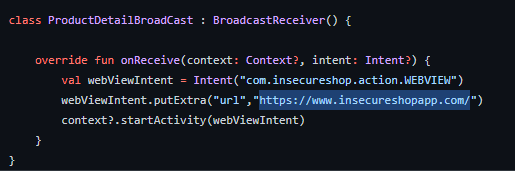
When it receives a corresponding intent, the ProductDetailBroadcast receiver starts an activity to open a web page using an implicit intent:
If we check the ProductAdapter class, we see that the PRODUCT_DETAIL intent is broadcasted whenever we click the more information option:

So, the workflow here is: user clicks on more info regarding a product -> launches a broadcast with the implicit PRODUCT_DETAIL broadcast -> receiver from ProductListing activity receives the intent -> ProductDetailBroadcast starts an activity using implicit intent.
The vulnerability here is that we can intercept the implicit intent in order to hijack the app’s flow and display our own attacker page. This is a problem because when users click on the more information button, they are redirected to a possibly malicious page and they might trust this page since it was opened by the trusted insecureshop app.
AndroidManifest.xml
MainActivity.kt
For this POC, we focused on intercepting the implicit activity start since we already have demonstrated intercepting implicit broadcast on the previous parts. As you can see, we have opened an attacker url in the context of the vulnerable application’s webview.
Last updated