😃Vulnerability #8: Insecure Broadcast Receiver
Exported activities are some possible attack vectors to look out for in the android manifest. In the target application, one such activity that has the attribute android:exported='true' is com.insecureshop.AboutUsActivity.
This is the activity that is opened when we try to click the about option in the pop-up menu. Seems innocent, but when we review the underlying code in jadx-gui we see the following:
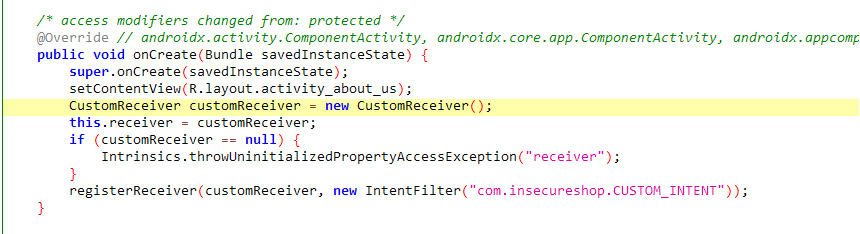
Upon onCreate, the activity registers a new CustomReceiver() which listens for the intent com.insecureshop.CUSTOM_INTENT

When it receives a broadcast with the custom intent filter, the CustomReceiver retrieves the value of the string extra web_url from the broadcasted intent, passes it as a url extra for the new intent then starts the following activity: WebView2Activity which just opens the url in a webview.
In case I haven’t mentioned it yet on part 1, you’ll be reading about intents a lot. Basically, intents are what allows different android app components to interact with each other. Read more about it from the documentation
This is vulnerable since the activity + receiver being exported means that attackers can send a com.insecureshop.CUSTOM_INTENT broadcast and open up an attacker-controlled url/content.
Last updated