😍Vulnerability #5: Insufficient URL Validation
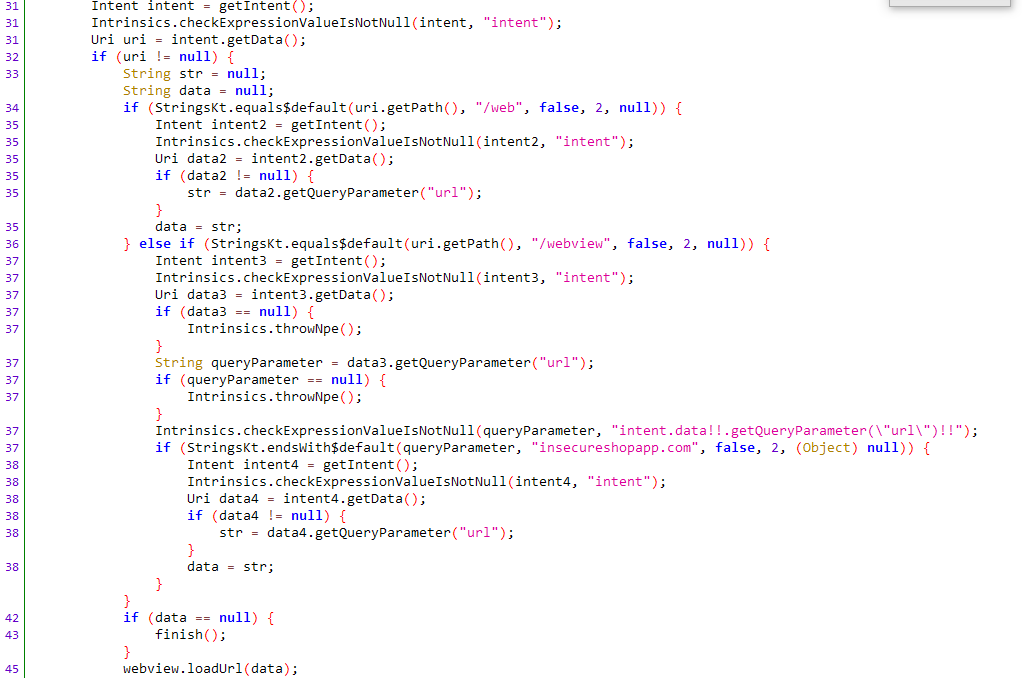
PreviousVulnerability #4: Lack of SSL Certificate ValidationNextVulnerability #6: Weak Host Validation
Last updated

Last updated
C:\Users\Aniket\Downloads\InsecureShop>adb shell am start -a android.intent.action.VIEW -c android.intent.category.BROWSABLE -d insecureshop://com.insecureshop/web?url=https://google.com
Starting: Intent { act=android.intent.action.VIEW cat=[android.intent.category.BROWSABLE] dat=insecureshop://com.insecureshop/web?url=https://google.com }